Prevent brute force attacks
A brute force attack is the simplest, yet efficient way of gaining access to secured data by trying various username and password combinations over and over again. Since password policies applied in Active Directory and Microsoft Entra ID often include locking an account after a certain number of failed login attempts, another goal that an attacker can pursue is to lock out user accounts.
For the reasons mentioned above, it is very important to protect your directory from brute force attacks, especially, when you have a Web interface accessible from the Internet. In this tutorial, you will learn how to configure protection against brute force attacks for the Web interface.
-
Open Adaxes Web interface configurator.
How { #collapse1}
-
On the computer where Web interface configurator is installed, open Windows Start menu.
-
Click Adaxes Web Interface Configurator.
The permissions to configure the Web interface are delegated via security roles. By default, only service administrators have the appropriate rights. To enable other users to configure the Web interface, grant them the corresponding permissions.
Grant permissions { #collapse2}
-
In Adaxes Administration console, right-click your Adaxes service, point to New and click Security Role.
-
Enter a name for the new security role and click Next.
-
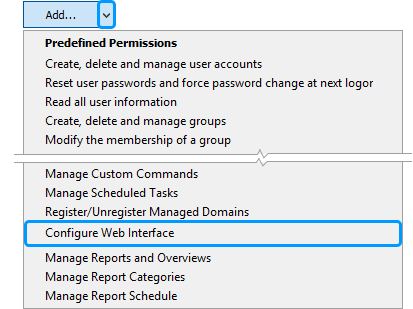
On the Permissions step, click the down arrow embedded into the Add button and click Configure Web Interface.
-
Click Next and follow the steps in the wizard.
-
-
In the top left corner, select the Web interface you want to customize.
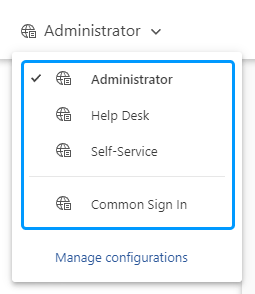
By default, all Web interfaces use the sign in settings of the Common Sign In page. If you want a particular Web interface to have different settings, select it in the list. Otherwise, select Common Sign In.
-
In the left navigation menu, click Sign in.
-
Scroll down to the Brute force protection section.
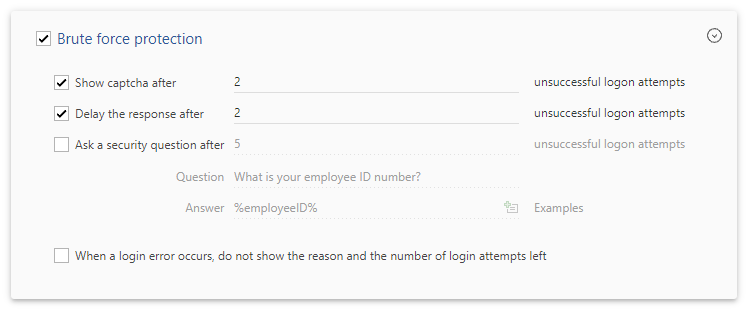
Configure the following options:
Show captcha
When this option is enabled, the Web interface will force users to solve a captcha (word verification image) after a certain number of failed login attempts.
Delay the response
When this option is enabled, after a certain number of failed login attempts, the Web interface will delay the responses by several seconds.
Ask security question
When this option is enabled, the Web interface will ask users to answer a question when they enter invalid credentials for a certain number of times. In the Question and Answer fields located below the option, you need to specify a question and the answer.
As an answer, you can specify a certain word or phrase known to users, for example, the name of the street where your company's headquarters is located. Alternatively, you can use value references (e.g. %department%) to specify an answer that will be specific to each user. Value references will be replaced with corresponding property values of the user account. For example, if you specify %department%, users will need to enter the name of their department specified in their account properties to answer the question.
More examples { #more_valref_examples}
-
%adm-ManagerFullName% – users will need to enter the full name of their manager.
-
%extensionAttribute1% – users will need to specify the text stored in the Extension Attribute 1 property of their account.
-
%employeeID%%telephoneNumber,6% – users will need to provide their employee ID and the first 6 digits of their telephone number.
If you use a value reference as the answer, and the corresponding property of the user account is empty, no answer will be accepted as correct.
When a login error occurs, do not show the reason and the number of login attempts left
By default, when a user provides invalid credentials, the Web interface shows a reason why a login attempt failed and the number of login attempts left according to the password policy applied to the user. When this option is enabled, such information is not displayed.
-
-
Save the changes.
Tracking
Each failed attempt to login to the Web interface is tracked by Adaxes. If the number of failed login attempts exceeds a certain threshold within a short period of time, to make further brute force login attempts less efficient, Adaxes adds an additional delay each time a user tries to log in.
How do I know the IP addresses from where suspicious activity originated? { #track_ip}
As soon as the threshold is reached, a warning containing IP addresses of the hosts from where the most of suspicious activity originated is logged in Adaxes Event Log. Warning sample:
Too many failed login attempts to Web interface SelfService. To protect you from a possible brute force attack, all subsequent login attempts will be processed with a delay.
The most of failed login attempts originated from the following IPs:
fe80::1dbd:465e:5fe6:3ea4%5
106.22.56.42
2001::db8::a0b::12f0::2255
...
How to access the log.
-
Open the Event Viewer on the computer where the Web interface is installed.
How { #collapse3}
-
Press Win+R.
-
Type eventvwr.msc.
-
Press Enter.
-
-
In the Event Viewer console tree, locate and click Adaxes.
If a failed login attempt was accidental, and there are no more failed attempts for the same username, password or IP address within a certain period of time, Adaxes removes it from the tracking system.

